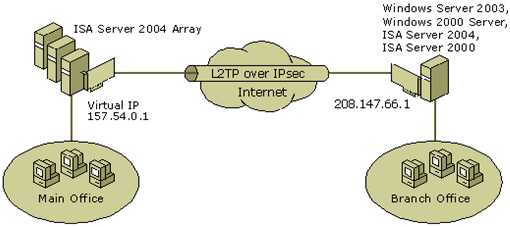
Layer 2 Tunneling Protocol (L2TP) is a tunneling protocol that is used to support a virtual private network (VPN). L2TP does not provide any encryption by itself, and is typically used with Internet Protocol Security (IPSec). IPSec provides the encryption and authentication whilst L2TP provides the end-to-end tunnel. L2TP was created primarily by Cisco and Microsoft to replace their L2F and PPTP protocols. L2TP/IPSec has been built-in to Windows 2000 and later versions and is available for older versions of Windows. Microsoft’s native client originally supported the Data Encryption Standard (DES). Microsoft has since removed DES as the default and now supports the Advanced Encryption Standard (AES) 256, AES 192, AES 128, and 3DES encryption algorithms. L2TP/IPSec is built-in to most modern operating systems such as Android, and iOS.